Which of the Following Statements Correctly Describes Biometric Methods
127-What ensures that the control mechanisms correctly implement the security policy for the entire life cycle of. Therefore these companies should not use the finger print.

Biometric Characteristic An Overview Sciencedirect Topics
Biometrics is a characteristic or a process used to identify one living person from another or from a non-living person using either biological or behavioral factors to automatically identify a person before allowing access this process is known as automated identification and data capture AIDC.
. They are the least expensive and provide the most protection They are the most expensive and provide the least protection They are the least expensive and provide the least protection They are the most expensive and provide the most protection. Quiz 5 Which of the following statements correctly describes biometric methods. 225-Which answer best describes a computer software attack that takes advantage of a previously unpublished.
Which of the following basic security components is used to support virtual smart cards. It is easy to duplicate and transfer someone elses fingerprints using biometrics. Biometric identifiers are the distinctive measurable characteristics used to label and describe.
Computer scientists are always. OSI is a set of rules that describes how security devices stop attacks. Biometrics make good authenticators because you must have an exact match to the computer.
A Polymorphic malware can change its characteristics every time it is transferred to a new system. Closed-Set Identification The person is. Which of the following statements correctly describes biometric methods.
HTTP is an example of a protocol handled at the Application layer of the OSI model. The OSI session layer handles connections between applications while the transport layer handles connections between systems. Which of the following statements correctly describes biometric methods.
They are the least expensive and provide the least protection. The controlling idea describes the advantages of a topic and the organizational pattern describes the disadvantages of the topic. They are expensive and provide the most protection.
Some believe that it provides more accurate result than fingerprint and will be the future of biometrics. 11 Questions Show answers. CandidateSubject A person who enters his biometric sample.
Biometric applications are generally categorized into three classifications. Which of the following statements correctly describes biometric methods. Biometrics are the most secure kinds of authenticators.
They are the most expensive and provide the most protection. Ear biometrics is one of the most accurate types of biometrics to authenticate a person. Which of the following statements correctly describes the malware characteristic of polymorphism.
They are the most expensive and provide the least protection. Which of the following statements correctly describes biometric methods. It is costly to get a biometric system up and running.
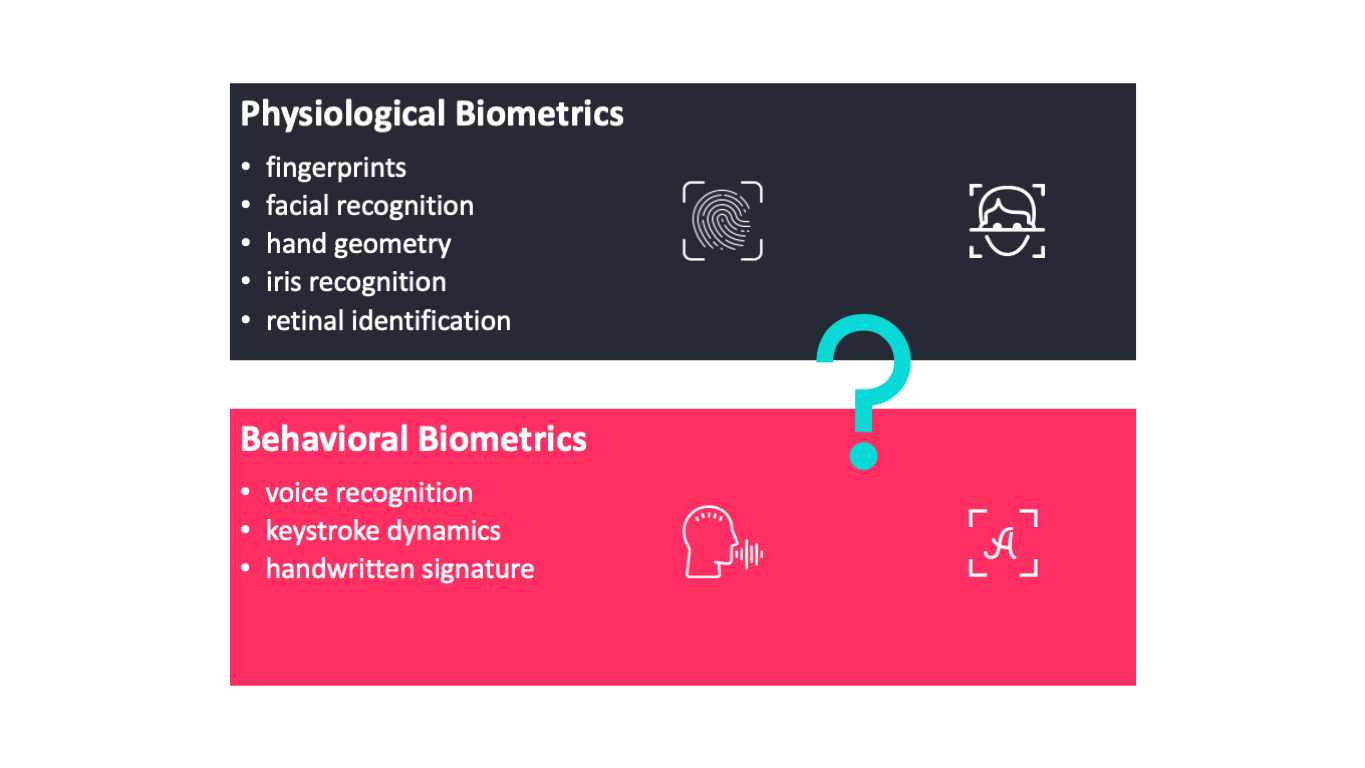
They are the least expensive and provide the most protection. Finger and hand geometry iris and palm imaging faceretina and voice recognition. They are the most expensive and provide the most protection.
B Polymorphic malware is designed to activate on a particular date remaining harmless until that time. Using virtual smart cards. They are the most expensive and provide the least protection.
First let s establish what exactly Biometrics is. Consider biometric methods that are used to authenticate a user. Biometric authentication or realistic authentication is used in computer science as a form of identification and access control.
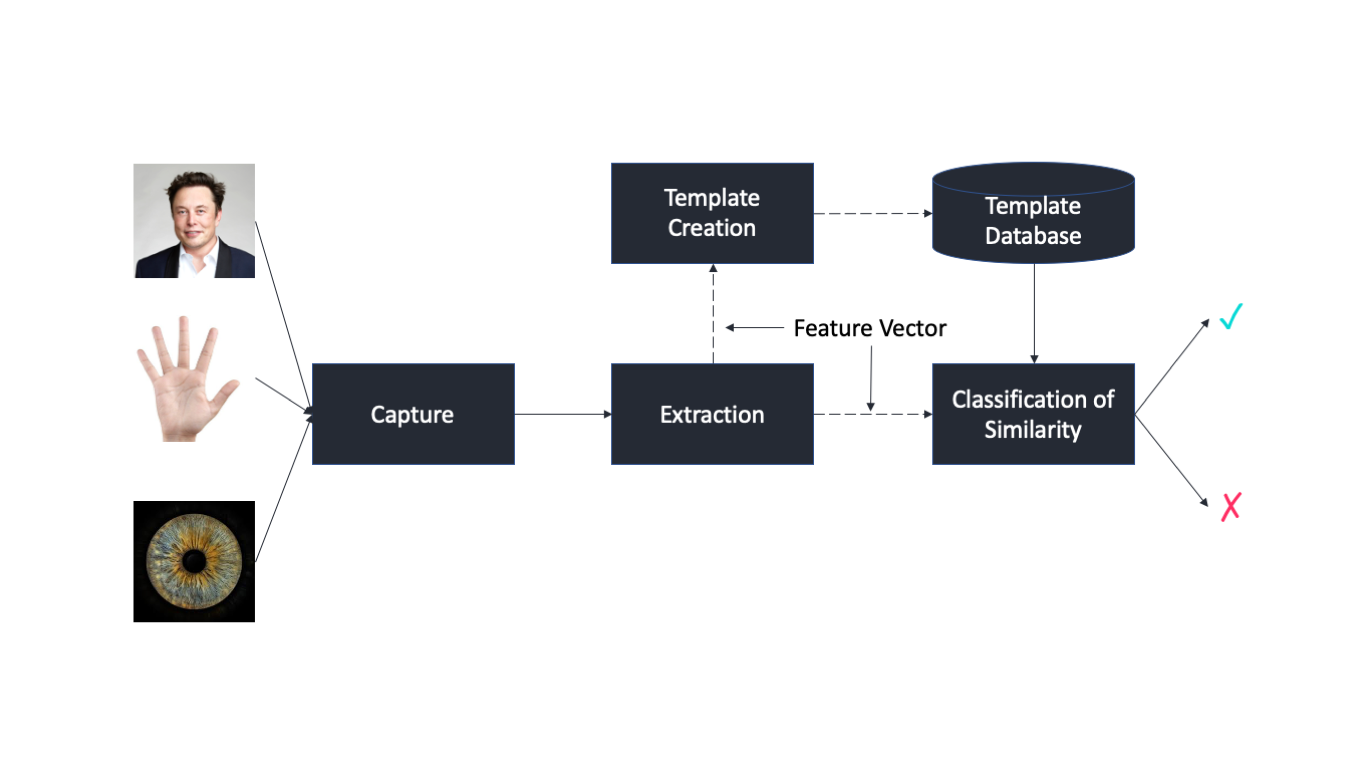
Biometric Template It is a digital reference of the distinct characteristics that are extracted from a biometric sample. They are the least expensive and provide the most protection. Which of the following statements is true about biometrics as an authentication method.
A low Crossover-Error-Rate CER D. 130-Which of the following statements pertaining to biometrics is false. Knowing that errors are possible which of the following would most likely result in a security breach.
Biometrics are beneficial for the following reasons. Biometrics are body measurements and calculations related to human characteristics. It is also used to identify individuals in groups that are under surveillance.
The finger print of those people working in Chemical industries are often affected. They are the least expensive and provide the most protection. Hard to fake or steal unlike passwords.
Face biometrics use aspects of the facial area to verify or identify an individual. Easy and convenient to use. Management of Biometrics Management of biometrics should address effective security for the collection distribution and processing of biometrics data encompassing.
Data integrity authenticity and non-repudiation Management of biometric data across its life cycle compromised of the enrollment transmission and storage verification identification and. Disadvantages however include the following. Which choice is the best description of the terms controlling idea and organizational patterns.
Finger geometry is a biometric process that captures features such as the shape and surface area of each finger its length width. Efficient because templates take up less storage. Generally the same over the course of a users life.
They are the least expensive and provide the least protection. The Disadvantages of Biometrics are the following. They are the least expensive and provide the least protection.
They are the most expensive and provide the most protection. When configuring two-factor authentication using digital certificates in Windows 10 on hardware with TPM chips which of the following methods is the most cost effective and secure. Gait recognition is a biometric technology method that analyzes an individual by how the way they walk like saunter swagger sashay etc.
They are the most expensive and provide the least protection.

Biometric Authentication Methods Fingerprints Facial Recognition Hand By Anh T Dang Towards Data Science

Two Main Types Of Biometrics Physical Vs Behavioral Biometrics Recfaces

Which Of The Following Statements Correctly Describes Biometric Methods Skillset
Biometric Authentication Methods Fingerprints Facial Recognition Hand By Anh T Dang Towards Data Science
Comments
Post a Comment